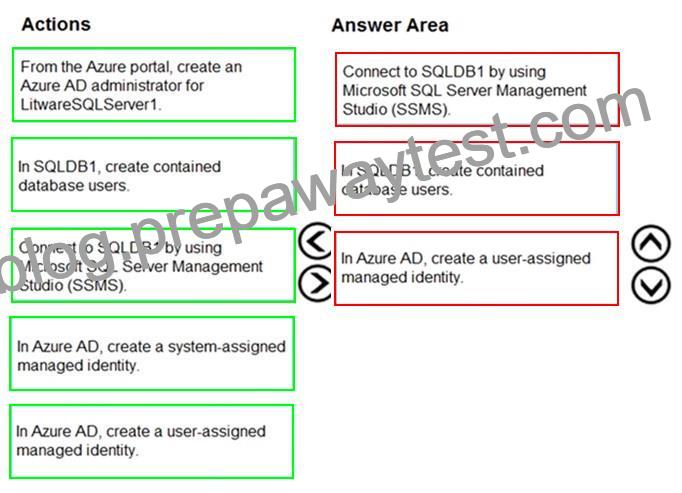
Explanation:
Step 1: Connect to SQLDB1 by using Microsoft SQL Server Management Studio (SSMS) Step 2: In SQLDB1, create contained database users.
Create a contained user in the database that represents the VM’s system-assigned identity.
Step 3: In Azure AD,create a system-assigned managed identity.
A system-assigned identity for a Windows virtual machine (VM) can be used to access an Azure SQL server. Managed Service Identities are automatically managed by Azure and enable you to authenticate to services that support Azure AD authentication, without needing to insert credentials into your code.
References:
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/tutorial-windows-vm-access-sql
Topic 2, Contoso
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab{s) and all Please note that once you submit your work by clicking the Next button within a lab.
Task 1:
You need to configure Azure to allow RDP connections from the Internet to a virtual machine named VM1. The solution must minimize the attack surface of VM1.
To complete this task, sign in to the Azure portal.
Task 2:
You need to add the network interface of a virtual machine named VM1 to an application security group named ASG1.
To complete this task, sign in to the Azure portal.
Task 3:
You need to perform a full malware scan every Sunday at 02:00 on a virtual machine named VM1 by using Microsoft Antimalware for Virtual Machines.
Task 4:
The developers at your company plan to create a web app named App103178O6 and to publish the app to htlps://www.contoso.com.
You need to perform the following tasks:
* Ensure that App10317806 is registered lo Azure Active Directory (Azure AD).
* Generate a password for App10317806.
Task 5:
You need to prevent administrative users from accidentally deleting a virtual network named VNET1. The administrative users must be allowed to modify the settings of VNET1.
Task 6:
You need to ensure that a user named user2103l7806 can manage the properties of the virtual machines in the RG1lod10317806 resource group. The solution must use the principle of least privilege.
Task 7:
You need to ensure that only devices connected to a 131.107.0.0/16 subnet can access data in the railod10317806 Azure Storage account, Task 8:
You need to email an alert to a user named
[email protected] if the average CPU usage of a virtual machine named VM1 is greater than 70 percent for a period of 15 minutes.
Task 9:
You need to collect all the audit failure data from the security log of a virtual machine named VM1 to an Azure Storage account.
To complete this task, sign in to the Azure portal.
This task might take several minutes to complete. You can perform other tasks while the task completes.
Task 10:
You need to prevent HTTP connections to the rg1lodl03l7806n1 Azure Storage account.
Task 11:
You need to ensure that the rg1lod10317806n1 Azure Storage account is encrypted by using a key stored in the KeyVault10317806 Azure key vault.
Task 12:
You need to create a new Azure Active Directory (Azure AD) directory named 10317806.onmicrosoft.com. The new directory must contain a user named userl103l7806.onmicrosoft.com who is configured to sign in by using Azure Multi-Factor Authentication (MFA).
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other question on this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next sections of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question on this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
Contoso, Ltd. is a consulting company that has a main office in Montreal and two branch offices in Seattle and New York.
The company hosts its entire server infrastructure in Azure.
Contoso has two Azure subscriptions named Sub1 and Sub2. Both subscriptions are associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
Technical Requirements
Contoso identifies the following technical requirements:
* Deploy Azure Firewall to VNetWork1 in Sub2.
* Register an application named App2 in contoso.com.
* Whenever possible, use the principle of least privilege.
* Enable Azure AD Privileged Identity Management (PIM) for contoso.com
Existing Environment
Azure AD
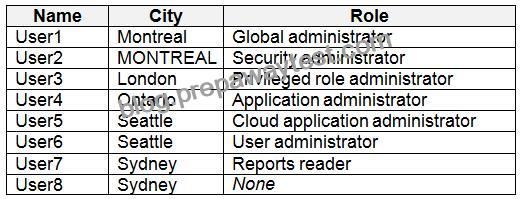
Contoso.com contains the users shown in the following table.
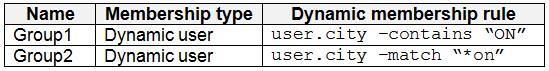
Contoso.com contains the security groups shown in the following table.
Sub1
Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6.
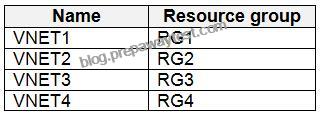
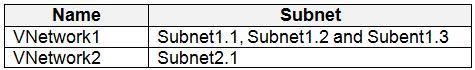
User2 creates the virtual networks shown in the following table.
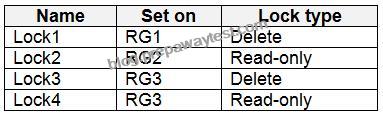
Sub1 contains the locks shown in the following table.
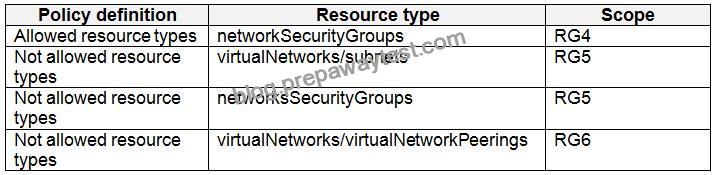
Sub1 contains the Azure policies shown in the following table.
Sub2
Sub2 contains the virtual machines shown in the following table.
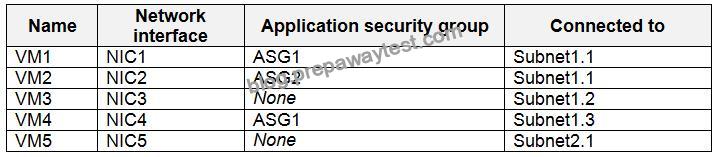
All virtual machines have the public IP addresses and the Web Server (IIS) role installed. The firewalls for each virtual machine allow ping requests and web requests.
Sub2 contains the network security groups (NSGs) shown in the following table.
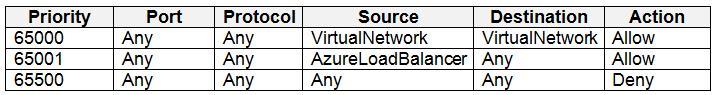
NSG1 has the inbound security rules shown in the following table.
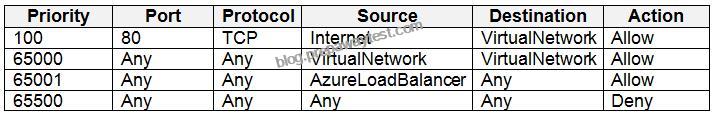
NSG2 has the inbound security rules shown in the following table.
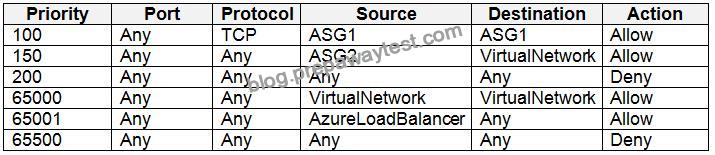
NSG3 has the inbound security rules shown in the following table.
NSG4 has the inbound security rules shown in the following table.
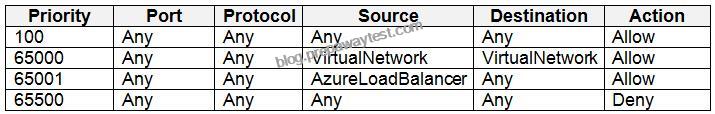
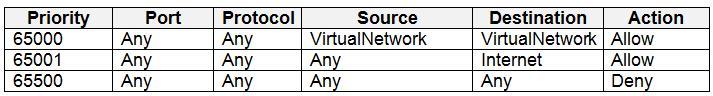
NSG1, NSG2, NSG3, and NSG4 have the outbound security rules shown in the following table.
Contoso identifies the following technical requirements:
* Deploy Azure Firewall to VNetwork1 in Sub2.
* Register an application named App2 in contoso.com.
* Whenever possible, use the principle of least privilege.
* Enable Azure AD Privileged Identity Management (PIM) for contoso.com.
